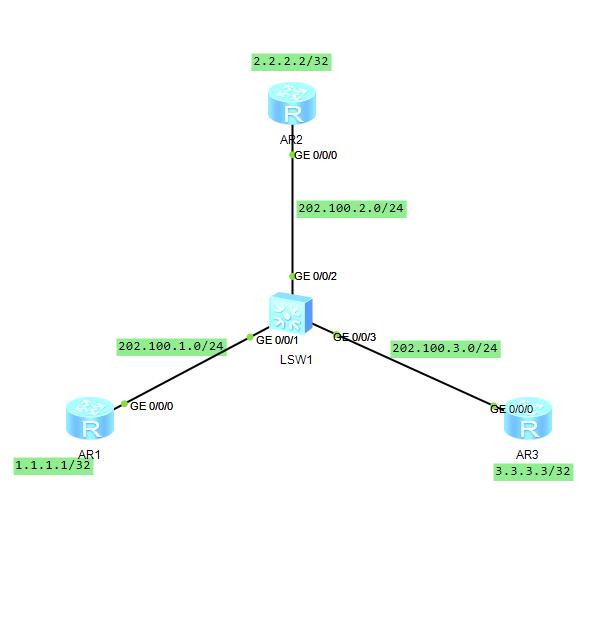
拓扑说明:只是在AR1-AR2上进行配置IPSec VPN,使用IKE方式协商密钥,在AR1和AR2的出接口上配置EasyIP。最终结果:只有AR1-AR2的环回接口互访使用IPsec VPN加密,访问其他的则不使用IPSec VPN。注意:路由器的本地接口无法进行NAT,需要外接其他设备来测试这个结果。
AR1:
#
sysname AR1
#
acl name NAT 3000
rule 5 deny ip source 1.1.1.1 0 destination 2.2.2.2 0 //这里拒绝NAT IPsec VPN中的网段
rule 10 permit ip source 1.1.1.1 0 //这里允许NAT的网段,本例中无法实现
acl name VPN 3001
rule 5 permit ip source 1.1.1.1 0 destination 2.2.2.2 0
#
ipsec proposal AAA
esp encryption-algorithm 3des
#
ike proposal 1
encryption-algorithm aes-cbc-192
authentication-algorithm md5
#
ike peer AAA v1
pre-shared-key simple arssra
ike-proposal 1
local-address 202.100.1.1
remote-address 202.100.2.2
#
ipsec policy AAA 1 isakmp
security acl 3001
ike-peer AAA
proposal AAA
#
interface GigabitEthernet0/0/0
ip address 202.100.1.1 255.255.255.0
ipsec policy AAA
nat outbound 3000
#
interface GigabitEthernet0/0/1
ip address 192.168.1.254 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
ip route-static 0.0.0.0 0.0.0.0 202.100.1.100
#AR2:
#
sysname AR2
#
acl name NAT 3000
rule 5 deny ip source 2.2.2.2 0 destination 1.1.1.1 0
rule 10 permit ip source 2.2.2.0 0.0.0.255 //这里等同AR1,无法实现功能
acl name VPN 3001
rule 5 permit ip source 2.2.2.2 0 destination 1.1.1.1 0
#
ipsec proposal AAA
esp encryption-algorithm 3des
#
ike proposal 1
encryption-algorithm aes-cbc-192
authentication-algorithm md5
#
ike peer AAA v1
pre-shared-key simple arssra
ike-proposal 1
local-address 202.100.2.2
remote-address 202.100.1.1
#
ipsec policy AAA 1 isakmp
security acl 3001
ike-peer AAA
proposal AAA
#
interface GigabitEthernet0/0/0
ip address 202.100.2.2 255.255.255.0
ipsec policy AAA
nat outbound 3000
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
#
ip route-static 0.0.0.0 0.0.0.0 202.100.2.100
#