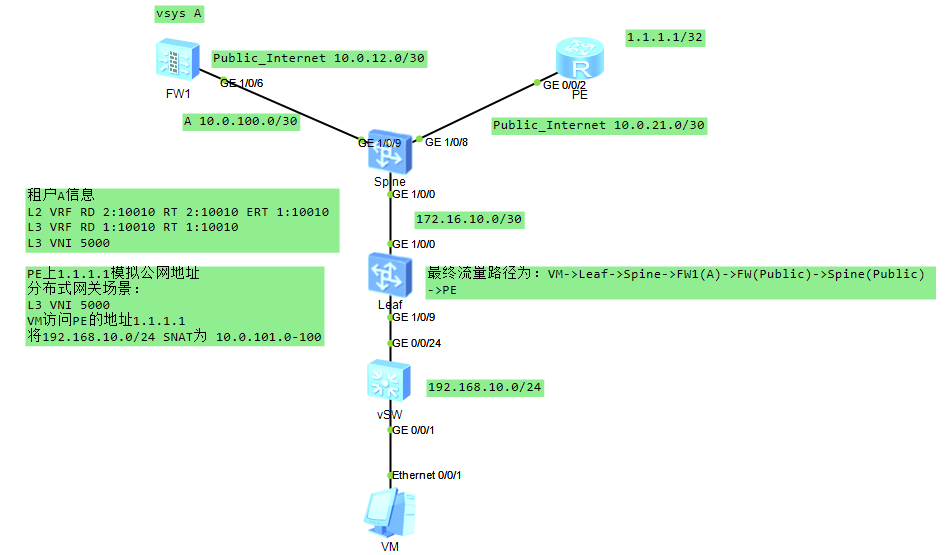
场景说明:比较符合现网配置,具体说明如图,缺少部分信息,这里比较关键的设备为防火墙、Spine,Spine作为Spine、Service-Leaf、Border-Leaf三合一设备
FW-根墙配置如下:
# sysname FW # vsys enable resource-class r0 # vsys name A 1 assign interface GigabitEthernet1/0/6.2 //给虚墙分配接口 assign global-ip 10.0.101.0 10.0.101.100 free //给虚墙A分配IP资源 # ip vpn-instance A ipv4-family ipv6-family # interface GigabitEthernet1/0/6 undo shutdown # interface GigabitEthernet1/0/6.1 vlan-type dot1q 11 ip address 10.0.12.2 255.255.255.252 ospf network-type p2p service-manage ping permit # interface GigabitEthernet1/0/6.2 vlan-type dot1q 12 ip binding vpn-instance A ip address 10.0.100.2 255.255.255.252 service-manage ping permit # interface Virtual-if0 # interface Virtual-if1 # interface NULL0 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface Virtual-if0 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/6.1 # firewall zone dmz set priority 50 # ospf 1 import-route static area 0.0.0.0 network 10.0.12.0 0.0.0.3 # ip route-static 10.0.100.0 255.255.255.252 vpn-instance A //配置指向虚墙的路由 ip route-static 10.0.101.0 255.255.255.0 vpn-instance A //配置指向虚墙的路由 # security-policy rule name Trust_Untrust source-zone trust destination-zone untrust action permit # return
FW-vSYS虚墙配置:
# switch vsys A # interface GigabitEthernet1/0/6.2 vlan-type dot1q 12 ip binding vpn-instance A ip address 10.0.100.2 255.255.255.252 service-manage ping permit # interface Virtual-if1 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/6.2 # firewall zone untrust set priority 5 add interface Virtual-if1 # firewall zone dmz set priority 50 # nat address-group SNAT 0 //配置SNAT地址池,这里用EasyNAT不行,因为出口为Virtual-if1 mode pat section 0 10.0.101.1 10.0.101.100 # multi-linkif mode proportion-of-weight # security-policy rule name Trust_Untrust source-zone trust destination-zone untrust action permit # nat-policy rule name SNAT_EasyIP source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 action source-nat address-group SNAT # ip route-static 0.0.0.0 0.0.0.0 public //配置默认路由到根墙 ip route-static 192.168.10.0 255.255.255.0 10.0.100.1 //配置明细路由指向Spine # return
Spine配置:
# sysname Spine # vlan batch 11 to 12 //创建互联VLAN # evpn-overlay enable # ip vpn-instance A //配置租户A的三层VRF ipv4-family route-distinguisher 1:10010 vpn-target 1:10010 export-extcommunity evpn vpn-target 1:10010 import-extcommunity evpn vxlan vni 5000 //指定租户A的L3 VNI为5000 # ip vpn-instance Public_Internet //配置通往公网的VRF ipv4-family route-distinguisher 1:1 vpn-target 1:1 export-extcommunity vpn-target 1:1 import-extcommunity # interface Vlanif11 ip binding vpn-instance Public_Internet ip address 10.0.12.1 255.255.255.252 ospf network-type p2p # interface Vlanif12 ip binding vpn-instance A ip address 10.0.100.1 255.255.255.252 # interface GE1/0/0 undo portswitch undo shutdown ip address 172.16.10.1 255.255.255.252 # interface GE1/0/8 undo portswitch undo shutdown ip binding vpn-instance Public_Internet ip address 10.0.21.1 255.255.255.252 ospf network-type p2p # interface GE1/0/9 undo shutdown port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 11 to 12 # interface LoopBack0 ip address 8.8.8.8 255.255.255.255 # interface Nve1 source 8.8.8.8 # interface NULL0 # bgp 100 peer 9.9.9.9 as-number 100 peer 9.9.9.9 connect-interface LoopBack0 # ipv4-family unicast undo peer 9.9.9.9 enable # ipv6-family unicast # ipv4-family vpn-instance A default-route imported //通过BGP下发默认路由 import-route static //引入静态路由 advertise l2vpn evpn //向EVPN实例发布IP路由 # l2vpn-family evpn undo policy vpn-target peer 9.9.9.9 enable peer 9.9.9.9 advertise irb //通告IRB路由 peer 9.9.9.9 reflect-client # ospf 1 vpn-instance Public_Internet area 0.0.0.0 network 10.0.12.0 0.0.0.3 network 10.0.21.0 0.0.0.3 # ospf 100 area 0.0.0.0 network 8.8.8.8 0.0.0.0 network 172.16.10.0 0.0.0.3 # ip route-static vpn-instance A 0.0.0.0 0.0.0.0 10.0.100.2 //配置静态路由指向虚墙A # return
Leaf配置:
# sysname Leaf # evpn-overlay enable # evpn # ip vpn-instance A ipv4-family route-distinguisher 1:10010 vpn-target 1:10010 export-extcommunity evpn vpn-target 1:10010 import-extcommunity evpn vxlan vni 5000 # bridge-domain 10 vxlan vni 10010 evpn route-distinguisher 2:10010 vpn-target 2:10010 export-extcommunity vpn-target 1:10010 export-extcommunity vpn-target 2:10010 import-extcommunity # interface Vbdif10 ip binding vpn-instance A ip address 192.168.10.254 255.255.255.0 arp collect host enable # interface MEth0/0/0 undo shutdown # interface GE1/0/0 undo portswitch undo shutdown ip address 172.16.10.2 255.255.255.252 # interface GE1/0/9.10 mode l2 encapsulation dot1q vid 10 bridge-domain 10 # interface LoopBack0 ip address 9.9.9.9 255.255.255.255 # interface Nve1 source 9.9.9.9 vni 10010 head-end peer-list protocol bgp # interface NULL0 # bgp 100 peer 8.8.8.8 as-number 100 peer 8.8.8.8 connect-interface LoopBack0 # ipv4-family unicast undo peer 8.8.8.8 enable # l2vpn-family evpn policy vpn-target peer 8.8.8.8 enable peer 8.8.8.8 advertise irb # ospf 100 area 0.0.0.0 network 9.9.9.9 0.0.0.0 network 172.16.10.0 0.0.0.3 # return