GRE(Generic Routing Encapsulation)
由于IPSec只能加密单播流量(IP流量),对语音、视频、动态路由协议等组播的流量无法加密。GRE是一种隧道封装技术。可以封装组播数据,并且可以配合IPSec使用,保证,语音、视频等组播业务的安全。
keepalive检测机制
默认Keepalive功能是未使能的,用于检测隧道是否对端可达。另外如果和ipsec一起配置 ,请最后加上可能导致tunnel口的协议down掉
IPSEC加密的GRE配置
拓扑如下:
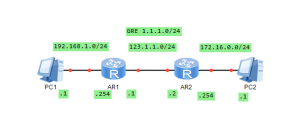
pc1=192.168.1.1/24
pc2=172.16.0.1/24
配置要求:使用ipsec和gre一起配置,达到PC1可以访问PC2,并且使用tracert可以明确看到走的是GRE隧道。
AR1配置如下:
#
sysname AR1
#
ipsec proposal ar1-proposal
#
ike proposal 1
#
ike peer ar1 v2
pre-shared-key simple ann
#
ipsec profile ar1-profile
ike-peer ar1
proposal ar1-proposal
#
interface GigabitEthernet0/0/0
ip address 123.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
ip address 192.168.1.254 255.255.255.0
#
interface Tunnel0/0/0
ip address 1.1.1.1 255.255.255.0
tunnel-protocol gre
keepalive period 3
source 123.1.1.1
destination 123.1.1.2
ipsec profile ar1-profile
#
ip route-static 0.0.0.0 0.0.0.0 Tunnel0/0/0
#
AR2配置如下:
#
sysname ar2
ipsec proposal ar2-proposal
#
ike proposal 1
#
ike peer ar2 v2
pre-shared-key simple ann
#
ipsec profile ar2-profile
ike-peer ar2
proposal ar2-proposal
#
interface GigabitEthernet0/0/0
ip address 123.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
ip address 172.16.0.254 255.255.255.0
#
interface Tunnel0/0/0
ip address 1.1.1.2 255.255.255.0
tunnel-protocol gre
keepalive period 3
source 123.1.1.2
destination 123.1.1.1
ipsec profile ar2-profile
#
ip route-static 0.0.0.0 0.0.0.0 Tunnel0/0/0
#
配置验证:PC1可以ping通PC2,并且通过路由跟踪可以明确看到数据流量通过GRE