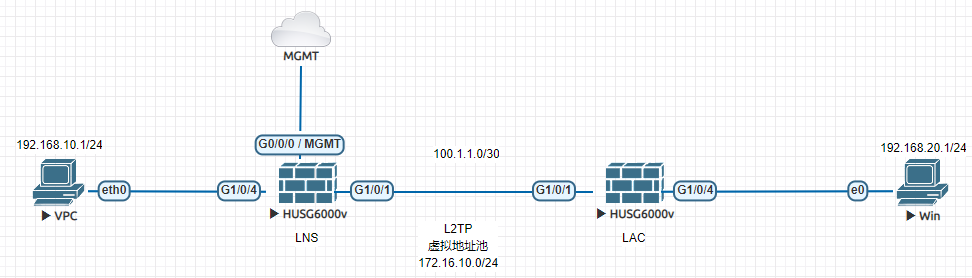
场景说明:LNS作为总部,LAC作为分支,分支与总部之间建立L2TP VPN,让分支可以访问总部的内部地址。
LNS配置:
sysname LNS # l2tp enable //开启L2TP功能 l2tp domain suffix-separator @ # ip pool L2TP //配置L2TP地址池 section 0 172.16.10.1 172.16.10.100 # aaa authentication-scheme default authentication-scheme admin_local authentication-scheme admin_radius_local authentication-scheme admin_hwtacacs_local authentication-scheme admin_ad_local authentication-scheme admin_ldap_local authentication-scheme admin_radius authentication-scheme admin_hwtacacs authentication-scheme admin_ad authentication-scheme admin_ldap authorization-scheme default accounting-scheme default service-scheme l2tp //配置服务规则绑定L2TP地址池,这里可以任意命名 ip-pool L2TP domain default service-type internetaccess ssl-vpn l2tp ike //这里一定要在domain中开启l2tp功能 internet-access mode auto-online reference user current-domain #此处配置了一个用户组名称为L2TP,配置了一个用户为ars且配置了密码,由于配置文件中看不到用户,因此没有显示 # l2tp-group 1 //配置L2TP组 tunnel password cipher %$%$=vm>Z}dHVPbl:DXrAPOUiW%.%$%$ //配置L2TP tunnel密码 allow l2tp virtual-template 0 remote A //关联L2TP的VT接口和tunnel名称A # interface Virtual-Template0 //配置VT接口 ppp authentication-mode chap remote service-scheme l2tp //关联服务规则 ip address 172.16.10.254 255.255.255.0 # interface GigabitEthernet1/0/0 undo shutdown service-manage ping permit # interface GigabitEthernet1/0/1 undo shutdown ip address 100.1.1.1 255.255.255.252 service-manage ping permit # interface GigabitEthernet1/0/4 undo shutdown ip address 192.168.10.254 255.255.255.0 service-manage ping permit # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/4 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/1 # firewall zone dmz set priority 50 add interface Virtual-Template0 # ip route-static 192.168.20.0 255.255.255.0 172.16.10.40 //这里需要写回程路由才能通讯,仅有写了回程路由LNS侧才能主动发起访问LAC侧终端。但是常规场景不建议做该方式,建议采用LAC侧做SNAT来解决,因为如果L2TP每次都变动IP的话则每次都需要修改路由,因此LAC侧采用SNAT方式将内部终端地址转换为LAC侧获取到的VT接口地址,由于L2TP会使用PPP协议中的地址获取功能和地址互推功能,因此两端会产生一个UNR路由达到通讯的目的。 # security-policy rule name Trust_Untrust_Permit source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 action permit rule name Trust_DMZ_Permit source-zone trust destination-zone dmz source-address 192.168.10.0 mask 255.255.255.0 destination-address 172.16.10.0 mask 255.255.255.0 //如果LAC侧采用SNAT,这里需要配置该地址 destination-address 192.168.20.0 mask 255.255.255.0 //如果LAC侧采用SNAT,这里不用配置该地址 action permit rule name DMZ_Trust_Permit source-zone dmz destination-zone trust source-address 172.16.10.0 mask 255.255.255.0 source-address 192.168.20.0 mask 255.255.255.0 destination-address 192.168.10.0 mask 255.255.255.0 action permit rule name Untrust_Local_Permit source-zone local source-zone untrust destination-zone local destination-zone untrust source-address 100.1.1.0 mask 255.255.255.252 destination-address 100.1.1.0 mask 255.255.255.252 action permit # return
LAC侧配置:
sysname LAC
#
l2tp enable //开启L2TP
#
l2tp-group 1 //配置L2TP组
tunnel password cipher %$%$Xll;:pDG^FSrY$"T(+GKKIBL%$%$ //配置tunnel 密码,需要与LNS侧设置的一致
tunnel name A //设定tunnel名称为A,需要与LNS侧一致
start l2tp ip 100.1.1.1 fullusername ars //配置根据IP接入L2TP,此处可以设定为域名,并配置全用户名,这里如果用户名不匹配的话,则无法正常建立VPN隧道
#
interface Virtual-Template0 //配置VT接口
ppp authentication-mode chap
ppp chap user ars
ppp chap password cipher %$%$C|gi~NA|R##"dWCS0L8I{HoK%$%$
ip address ppp-negotiate
call-lns local-user ars //配置LAC自主拨号用户名,该用户需要与ppp user一致
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.1.1.2 255.255.255.252
service-manage ping permit
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 192.168.20.254 255.255.255.0
service-manage ping permit
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface Virtual-Template0
#
ip route-static 192.168.10.0 255.255.255.0 Virtual-Template0 //配置到LNS侧的业务路由
#
user-interface con 0
authentication-mode password
set authentication password cipher $1c$uMM_BG!%M:$Q+N<0jBRb0!o)C)'@Hj6ASlG%9-a7&9Q"cK!~ig&$
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
security-policy
rule name Untrust_Local_Permit
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 100.1.1.0 mask 255.255.255.252
destination-address 100.1.1.0 mask 255.255.255.252
action permit
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
action permit
rule name Trust_DMZ_Permit
source-zone trust
destination-zone dmz
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name DMZ_Trust_Permit
source-zone dmz
destination-zone trust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
#
nat-policy //配置SNAT场景,如果LNS侧不需要主动访问LAC侧终端,建议通过该方式达到互通目的,减少LNS侧路由配置。
rule name Trust_DMZ_EasyIP
source-zone trust
egress-interface Virtual-Template0
source-address 192.168.20.0 mask 255.255.255.0
action source-nat easy-ip
return
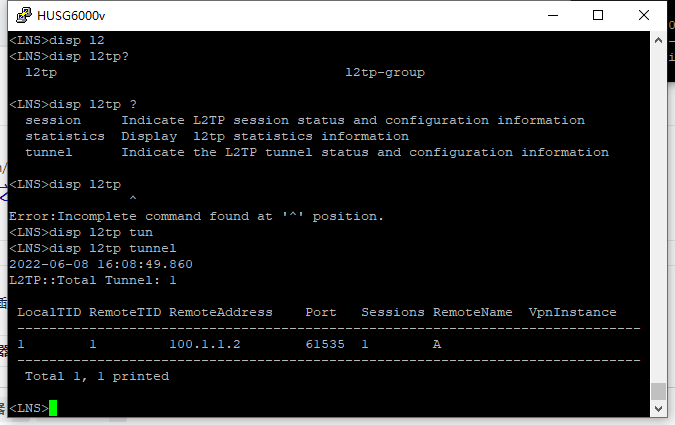
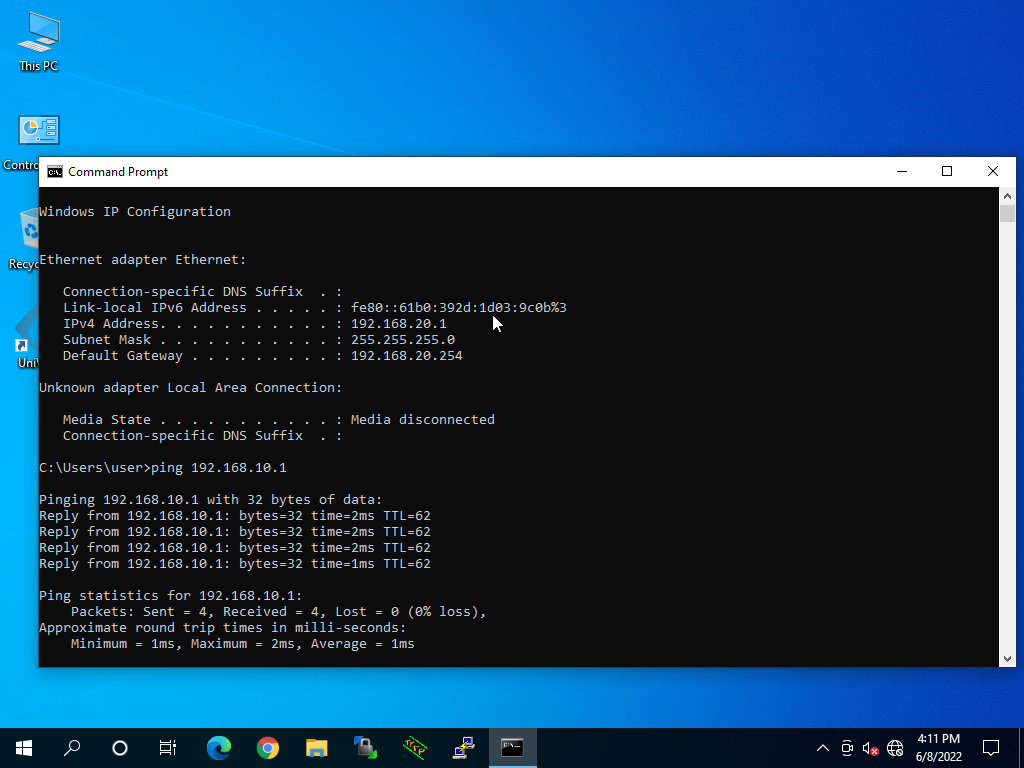
配置结果:
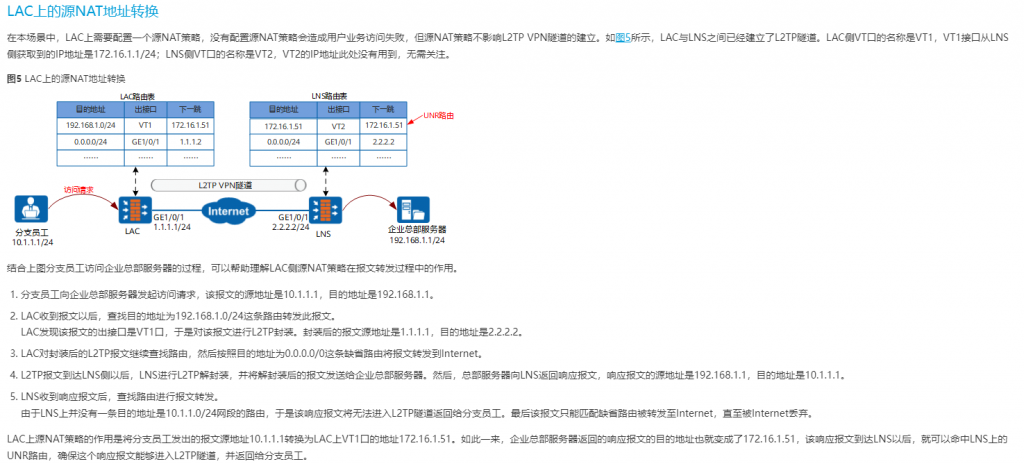
关于SNAT应用: