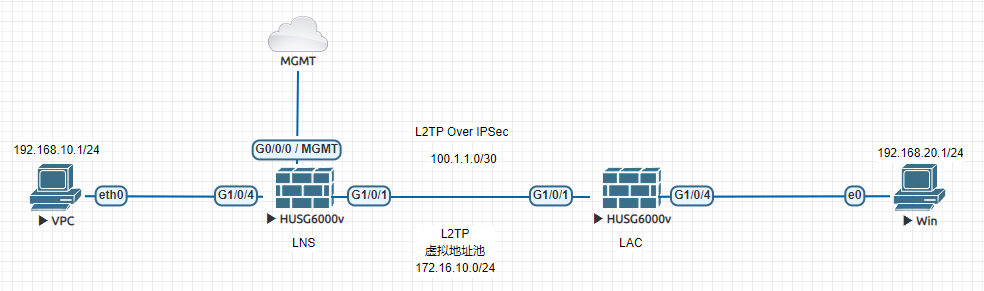
场景说明:LNS与LAC之间建立CALL-LNS的L2TP VPN,由于L2TP缺少对数据的安全保护,因此采用IPSEC保护L2TP交互的流量,使LAC侧的PC可以访问LNS内部的设备。
LNS配置:
sysname LNS
#
l2tp enable //开启L2TP功能
l2tp domain suffix-separator @
#
acl number 3000 //设置IPSEC保护的数据流,由于是先封装L2TP,因此保护的是建立L2TP隧道的地址
rule 5 permit udp source 100.1.1.1 0 destination 100.1.1.2 0 destination-port eq 1701
rule 10 permit udp source 100.1.1.1 0 source-port eq 1701 destination 100.1.1.2 0
#
ipsec proposal A //设置IPSEC安全提议
encapsulation-mode transport //如果没有NAT-T场景,那么建议选择传输模式,选择隧道模式的话,还会再次封装一层头部,可能导致报文过长形成分片,降低处理效率,消耗处理资源
esp authentication-algorithm sha2-256 //设置IPSEC的认证算法
esp encryption-algorithm aes-256 //设置IPSEC的加密算法
#
ike proposal 1 //设置IKE安全提议
encryption-algorithm aes-256 //设置加密算法
dh group14 //设置DH组,越大长度越长
authentication-algorithm sha2-256 //设置认证算法
authentication-method pre-share //设置认证方式为预共享密钥
integrity-algorithm hmac-sha2-256 //设置IKE协商的完成性算法
prf hmac-sha2-256 //设置伪随机数使用的算法
#
ike peer A //设置IKE PEER
pre-shared-key %^%#$g^0*e4&@N3R_:~'GvyE"w"R2Ux#Q=f=W~2ZI{wB%^%# //预共享密码
ike-proposal 1 //绑定IKE安全提议
remote-address 100.1.1.2 //设定IKE对等体的地址
#
ipsec policy A 1 isakmp //设置安全策略,表示使用IKE方式协商ipsec sa
security acl 3000 //设定感兴趣流
ike-peer A //绑定IKE PEER
proposal A //绑定IPSEC安全提议
sa trigger-mode auto //IPSEC隧道建立方式为自动触发,其实这一步没必要配置,因为L2TP建立后,会有保活报文进行交互。
#
aaa
service-scheme l2tp //设置安全规则
ip-pool l2tp //绑定地址池
domain default
service-type internetaccess l2tp ike //开启认证域接入,允许L2TP和IKE
#
user-manage group /default/l2tp //建立一个用户组
#
user-manage user ars //建立l2tp用户
parent-group /default/l2tp //设置用户组
bind mode unidirectional //IP/MAC单向绑定,变相的是不绑定
password xxxxxxxx //设置密码
#
ip pool l2tp //建立L2TP地址池
section 0 172.16.10.1 172.16.10.253
#
l2tp-group 1 //设置L2TP组
tunnel password cipher %$%$H/5<7v3/388=wu2P0;M/73,a%$%$ //设置隧道密码
allow l2tp virtual-template 0 remote AAA //绑定相应的VT接口和隧道名称
#
interface Virtual-Template0 //设置VT接口
ppp authentication-mode chap //PPP链路的认证方式为CHAP
remote service-scheme l2tp //绑定相应的服务规则
ip address 172.16.10.254 255.255.255.0
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.1.1.1 255.255.255.252
ipsec policy A
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 192.168.10.254 255.255.255.0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
#
firewall zone name l2tp id 4
set priority 49
add interface Virtual-Template0
#
security-policy
rule name Untrust&Local_L2TP_Permit //放行L2TP和IPSEC IKE建立的策略
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 100.1.1.0 mask 255.255.255.252
destination-address 100.1.1.0 mask 255.255.255.252
service esp
service l2tp
service protocol udp destination-port 500
action permit
rule name Trust_Untrust_Permit //允许内网访问互联网
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name l2tp_Trust_Permit //允许L2TP侧访问内网
source-zone l2tp
destination-zone trust
source-address 172.16.10.0 mask 255.255.255.0 //设置如果LAC使用了SNAT,就写L2TP的地址池,如果没有应用则需要LNS写回程路由,比较麻烦,建议采用SNAT方式。
destination-address 192.168.10.0 mask 255.255.255.0
action permit
#
return
LAC配置:
sysname LAC
#
l2tp enable
#
acl number 3000
rule 5 permit udp source 100.1.1.2 0 destination 100.1.1.1 0 destination-port eq 1701
rule 10 permit udp source 100.1.1.2 0 source-port eq 1701 destination 100.1.1.1 0
#
ipsec proposal A
encapsulation-mode transport
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer A
pre-shared-key %^%#Mx4u5o{H>*hl9iNWj0M/MlKxVtm$pN9Dm8E/XYI4%^%#
ike-proposal 1
remote-address 100.1.1.1
#
ipsec policy A 1 isakmp
security acl 3000
ike-peer A
proposal A
sa trigger-mode auto
#
#
l2tp-group 1
tunnel password cipher %$%$)I{~ItFIw7tpM80u1PH4~``;%$%$
tunnel name AAA //设定隧道名称
start l2tp ip 100.1.1.1 fullusername ars //设备本端到对端建立L2TP tunnel的地址和用户名
#
interface Virtual-Template0
ppp authentication-mode chap
ppp chap user ars
ppp chap password cipher %$%$_QiyYx(le:Li{[/U]xk,/s&~%$%$
ip address ppp-negotiate
call-lns local-user ars
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.1.1.2 255.255.255.252
ipsec policy A
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 192.168.20.254 255.255.255.0
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
#
firewall zone name l2tp id 4
set priority 51
add interface Virtual-Template0
#
api
#
ip route-static 192.168.10.0 255.255.255.0 Virtual-Template0
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
action permit
rule name Trust_l2tp_Permit
source-zone trust
destination-zone l2tp
source-address 192.168.20.0 mask 255.255.255.0
action permit
rule name Untrust&Local_L2TP_Permit
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 100.1.1.0 mask 255.255.255.252
destination-address 100.1.1.0 mask 255.255.255.252
service esp
service l2tp
service protocol udp destination-port 500
action permit
#
nat-policy //配置SNAT策略,L2TP访问LNS侧进行SNAT转换
rule name Trust_l2tp_EasyIP_SNAT
source-zone trust
egress-interface Virtual-Template0
source-address 192.168.20.0 mask 255.255.255.0
action source-nat easy-ip
#
return
实验结果:
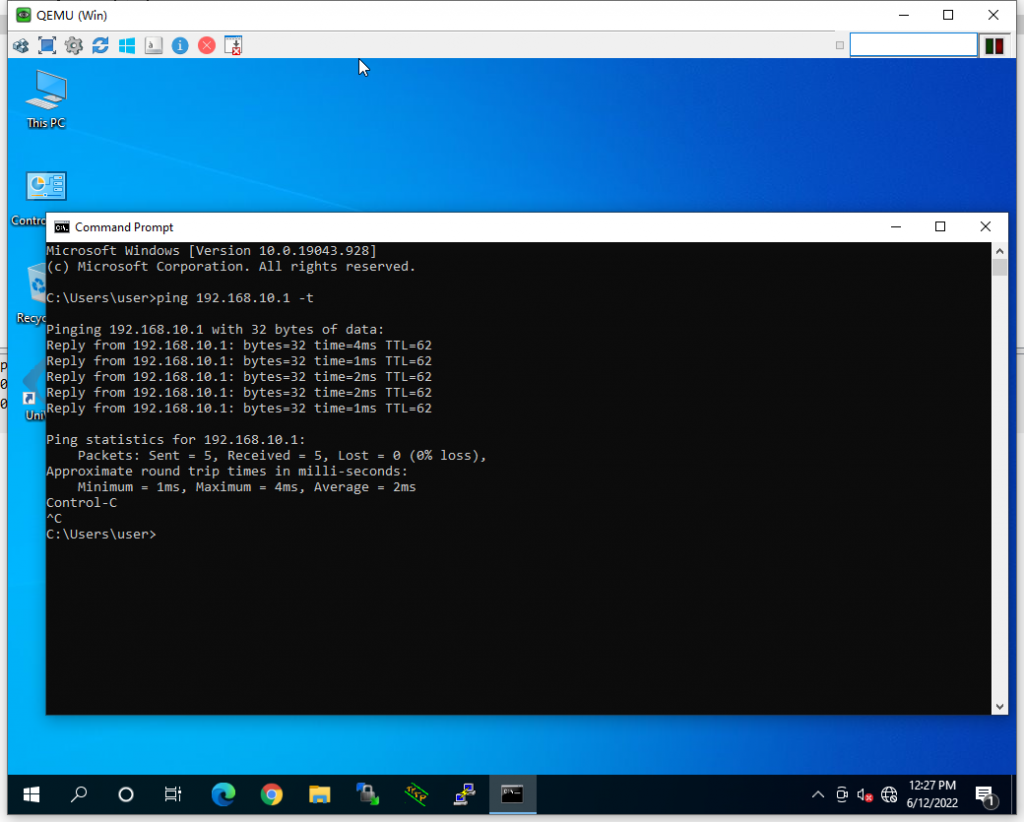
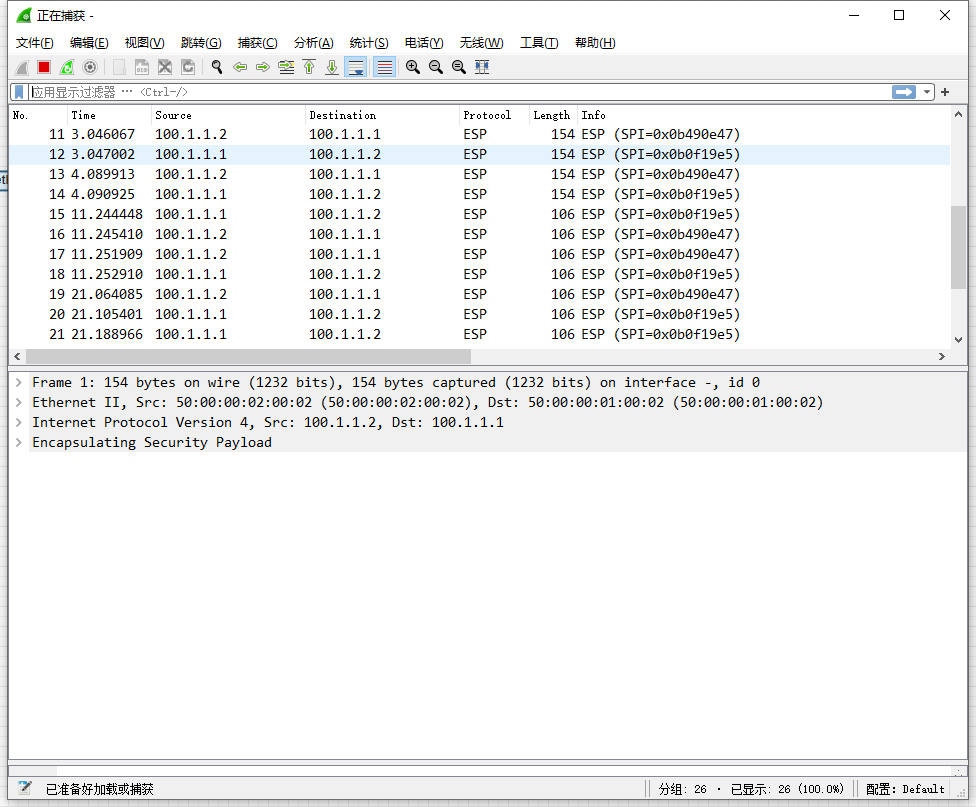
根据抓包看结果,数据是被IPSEC加密的,同时LAC侧客户端也可以访问LNS。