使用USG6000当做路由器配置,做easyip的nat配置与nat server配置。
使Client使用NAT的方式访问内部Server 80端口。
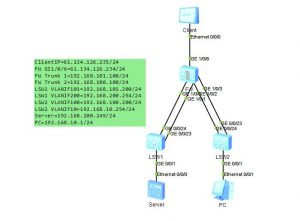
拓扑如下:
interface Eth-Trunk1
ip address 192.168.101.100 255.255.255.0
service-manage ping permit
#
interface Eth-Trunk2
ip address 192.168.100.100 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/0
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/1
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/2
undo shutdown
eth-trunk 2
#
interface GigabitEthernet1/0/3
undo shutdown
eth-trunk 2
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 61.134.126.234 255.255.255.0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface Eth-Trunk2
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/6
#
firewall zone dmz
set priority 50
add interface Eth-Trunk1
#
ip route-static 0.0.0.0 0.0.0.0 61.134.126.235
ip route-static 192.168.10.0 255.255.255.0 192.168.100.200
ip route-static 192.168.100.0 255.255.255.0 192.168.100.200
ip route-static 192.168.101.0 255.255.255.0 192.168.101.200
ip route-static 192.168.200.0 255.255.255.0 192.168.101.200
#
undo ssh server compatible-ssh1x enable
#
nat server server_www 0 protocol tcp global 61.134.126.234 www inside 192.168.2
00.249 www no-reverse
#
nat address-group addrgroup1 0
mode pat
route enable
section 0 61.134.126.234 61.134.126.234
#
multi-interface
mode proportion-of-weight
#
security-policy
rule name access_internet_trust
source-zone trust
destination-zone untrust
source-address 192.168.10.0 24
source-address 192.168.100.0 24
action permit
rule name access_internet_dmz
source-zone dmz
destination-zone untrust
source-address 192.168.101.0 24
source-address 192.168.200.0 24
action permit
rule name local_trust
source-zone local
destination-zone trust
action permit
rule name local_dmz
source-zone local
destination-zone dmz
action permit
rule name access_server_dmz
source-zone untrust
destination-zone dmz
destination-address 192.168.200.249 32
action permit
#
nat-policy
rule name easyip_trust
source-zone trust
destination-zone untrust
source-address 192.168.10.0 24
source-address 192.168.100.0 24
action nat easy-ip
rule name easyip_dmz
source-zone dmz
destination-zone untrust
source-address 192.168.101.0 24
source-address 192.168.200.0 24
action nat easy-ip
rule name nat_server_dmz
source-zone dmz
destination-zone dmz
source-address 192.168.200.249 32
action nat address-group addrgroup1
#
return
检查配置使用Server开启WEB服务,Client可以通过NAT访问内部服务器。