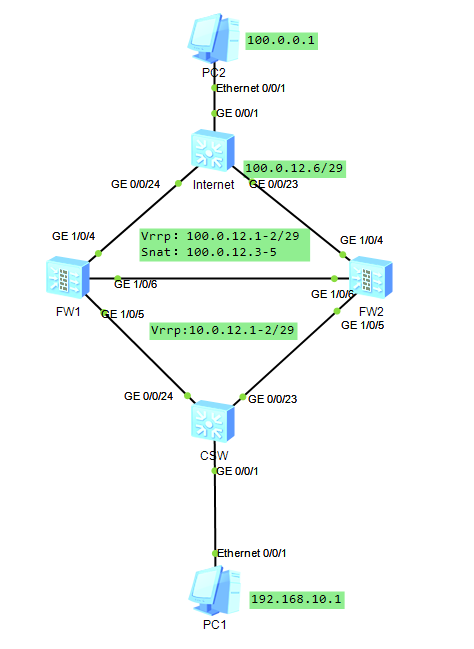
场景说明:某公司跟运营商申请了公网地址100.0.12.0/29,其中100.0.12.6作为运营商下一跳,100.0.12.1-5为购买地址,其中防火墙负载分担使用100.0.12.1-2两个IP,其余100.0.12.3-5作为SNAT使用使内网PC1可以访问公网。
FW-1配置如下:
# sysname FW-1 # hrp enable hrp interface GigabitEthernet1/0/6 remote 1.1.1.2 //配置HRP接口及地址,指定remote采用UDP封装HRP报文,不指定remote-ip则采用组播发送通过VRRP封装 hrp mirror session enable //开启会话同步 hrp nat resource primary-group //负载分担场景为了防止SNAT后的端口冲突需要配置该命令,备墙需要配置hrp nat resource secondary-group hrp track interface GigabitEthernet1/0/4 hrp track interface GigabitEthernet1/0/5 # interface GigabitEthernet0/0/0 undo shutdown ip binding vpn-instance default ip address 192.168.0.1 255.255.255.0 alias GE0/METH # interface GigabitEthernet1/0/4 undo shutdown ip address 10.0.21.1 255.255.255.252 vrrp vrid 3 virtual-ip 100.0.12.1 255.255.255.248 active vrrp vrid 4 virtual-ip 100.0.12.2 255.255.255.248 standby link-group 1 //配置link-group联动组,当组内一个端口down后,其他组内成员端口也会down,本场景可以不配置link-group service-manage ping permit # interface GigabitEthernet1/0/5 undo shutdown ip address 10.0.12.3 255.255.255.248 vrrp vrid 1 virtual-ip 10.0.12.1 active vrrp vrid 2 virtual-ip 10.0.12.2 standby link-group 1 service-manage ping permit # interface GigabitEthernet1/0/6 undo shutdown ip address 1.1.1.1 255.255.255.252 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/5 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/4 # firewall zone dmz set priority 50 add interface GigabitEthernet1/0/6 # ip route-static 0.0.0.0 0.0.0.0 100.0.12.6 ip route-static 192.168.10.0 255.255.255.0 10.0.12.5 # nat address-group SNAT 0 mode pat route enable //自动生成unr的黑洞路由 section 0 100.0.12.3 100.0.12.5 # security-policy rule name Trust_Untrust_Permit source-zone trust destination-zone untrust action permit # nat-policy rule name Trust_Untrust_Snat source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 action source-nat address-group SNAT return
备墙和主墙配置差不多,唯一区别就是hrp nat resource secondary-group。
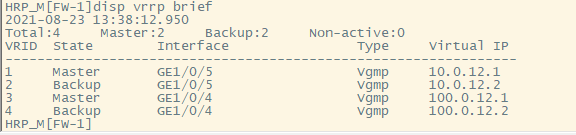
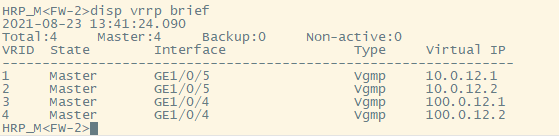
vrrp结果如下:
核心交换机上的默认路由指向两个虚地址10.0.12.1和10.0.12.2,无需配置track来监控路由是否可达
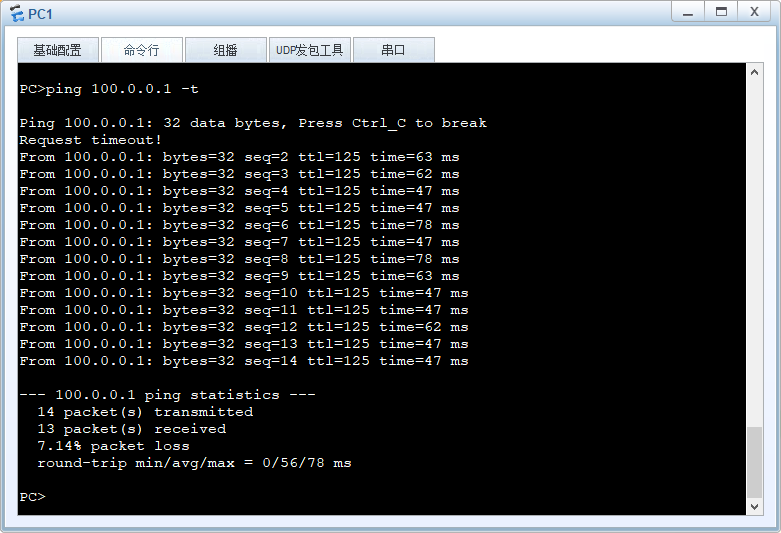
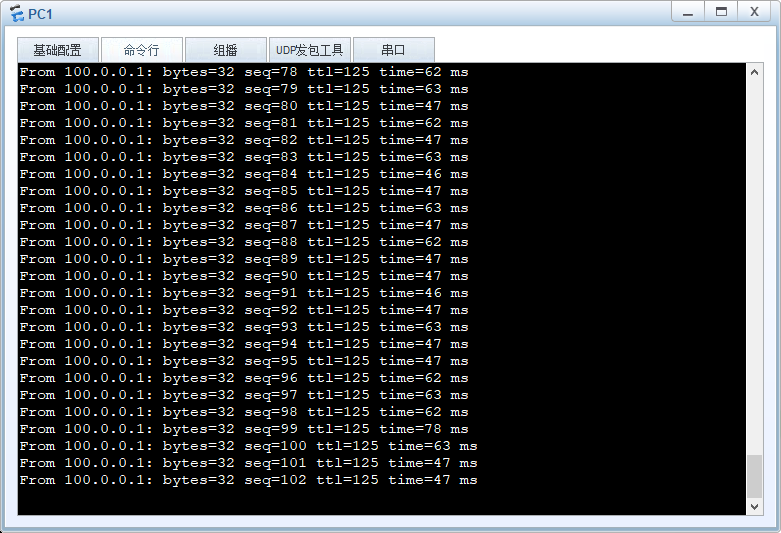
实验结果:
模拟主墙GE1/0/4接口故障后主备发生切换:
备墙成为MASTER承担流量转发。